Information Fusion Schemes for Reliable Biometric System?
Aranuwa FO*
Department of Computer Science, Adekunle Ajasin University, Akungba Akoko,Ondo State, Nigeria
*Address for Correspondence: Aranuwa FO, Department of Computer Science, Adekunle Ajasin University, Akungba Akoko,Ondo State, Nigeria, Tel: +234-703-134-1911; ORCid: https://orcid.org/0000-0002-3413-0554; E-mail: felix.aranuwa@aaua.edu.ng
Submitted: 05 February 2020; Approved: 24 February 2020; Published: 28 February 2020
Citation this article: Aranuwa FO. Information Fusion Schemes for Reliable Biometric System. American J Biom Biostat. 2020;4(1): 001-005.
Copyright: © 2020 Aranuwa FO. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited
Keywords: Information fusion; Spoof attacks; Multiple biometrics; Authentication; Security systems
Download Fulltext PDF
Globally, biometric system is becoming increasingly more popular in many authentication applications due to its performance and the basic premise that every person can be identified by his or her intrinsic physiological or behavioral traits. The technology is largely used for identification access control and in surveillance system. In many biometric systems, the choice and sources of evidence used are strongly dependent on the application scenario and the design decisions. Meanwhile, studies have revealed that a biometric system that uses a single biometric source or trait for authentication has this tendency to face with problems related to noise in sensed data, non-universality, susceptibility to spoof attacks and large intra-class variations. Therefore, it is believed that some of the shortcomings of uni-biometric systems can be overcome and much higher accuracy achieved by integrating the evidences from multiple biometric sources or traits for establishing identity. Researchers at different levels have proposed and combined the outputs of two or more classifiers in the domain. Yet, the issue of efficient information fusion of these evidences remains an obvious concept that attract research attention. Hence, this work investigated and presents different classifier fusion techniques and design level scenarios that are viable for reliable biometric recognition system. Based on the research investigation, Dempster Shafer’s rule of combination and fusion at the match-score level were considered the preferred information fusion technique and design scheme respectively due to their pragmatic and performance physiognomies.
Introduction
Biometric can be described as a technology that uses the biological characteristics of a person to identify him or her. The term biometrics is derived from the Greek words’ bio meaning life and metric meaning to measure [1]. Biometric identifiers are often categorized as physiological and behavioral characteristics [2]. The physiological characteristics are related to the shape or the structural pattern of the body. Examples include, but not limited to fingerprint, palm veins, face recognition, DNA, palm print, hand geometry, iris recognition, retina and odour/scent, while behavioral characteristics are related to the behavioral pattern of a person, example include, but not limited to typing rhythm, gait, and voice [3].
The technology globally has emerged as a reliable and highly secure identification and personal verification solutions in our environment today because of its performance, uniqueness and consistency over time [4]. Notable application areas include: access control, authentication, forensic investigation and so on. In many biometric systems, the choice and sources of evidence to be used are strongly dependent on the application scenario and the design decisions. By application strategy, when a single trait is used in any application it is referred to as uni-biometric system, while combination of two or more sources or traits in an application is referred to as multiple biometrics [5]. Combination of multiple modalities in biometric becomes a good strategy to improve its performance and reliability as it is considered to be intrinsically robust against noisy data and spoof attacks [6]. However, the issue of efficient information integration/fusion of these evidences obtained from multiple traits or sources remains an obvious concept that attract research attention. Hence, this research work investigated and presents different classifier fusion schemes and design scenarios viable for reliable biometric recognition system.
Literature Review
Biometric processing modes
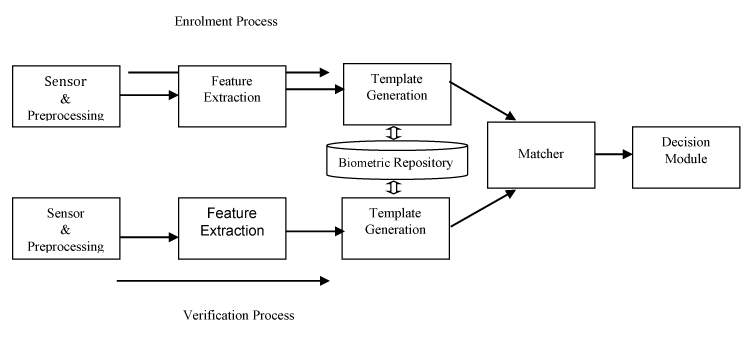
Generally, biometric system involves two basic biometric processing modes namely, the enrolment and verification modes. The two basic modes involve sub stages for its processes as depicted in figure1.
During enrolment process, biometric information from an individual is captured and stored in the biometric repository. In subsequent uses, biometric information is retrieved and compared with the information stored at the time of enrolment to validate or confirm whether the individual is the person claim to be during verification. According to [7] five modules are involved in each mode, the first is the sensor module which involves the capturing of biometric data from an individual using an appropriate device, the second is the feature extraction responsible for the processing and extraction of salient features from the data acquired. The third module is the biometric repository that house the reference models called (template) for all the users in the model database. The template for each user is labelled with its confidence score for confirmation during the verification process. The fourth is the matching module, this module compares a claimed identity with the reference models stored in the database to generate match scores. The fifth is the decision module which uses the match scores generated in the match module to validate a claimed identity and determine whether to reject or accept the claim.
Information fusion schemes in multiple-biometric
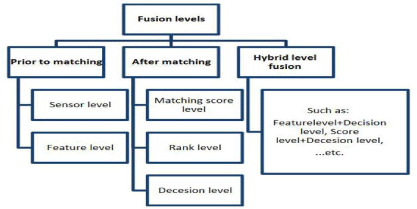
Systems Sources and fusion scenario in multiple biometric systems can be classified into one of the following six categories: Multiple sensors, multiple representations, multiple samples, multiple instances, multiple traits and hybrid [4]. The fusion of evidences from these sources generally can take place at four major levels, namely: The sensor level, feature level, score level and decision level. These levels are broadly categorized into: Pre-classification scheme or fusion before matching and post-classification scheme or fusion after matching [5,8] (Figure 2).
The fusion levels classification are classified below
Fusion prior to matching (Pre-classification): Fusion levels in this category consolidate evidences before matching. They are:
• The sensor level fusion: In this level, biometric data are consolidated at sensor level and new biometric data generated out of this merger. The data may be sampled from a single sensor or multiple compatible sensors. This level of fusion is also known as data level fusion or image level fusion. Fusion at this level may not be possible if the data instances and resolution are incompatible. For example: Fusion of Infrared (IR) and visible face Images for face recognition.
• Feature level fusion: In feature level fusion, feature sets originating from multiple information sources are integrated into a new feature set. Feature set from this level contains richer information about the input biometric data than any other levels. However, integration at this level is difficult to achieve in practice because concatenating two features at this level may lead to dimensionality problem thereby required specific fusion algorithm to form a composite feature set.
Fusion after matching (Post- classification): The fusion scheme integrates evidences after matching. The following fusion levels belongs to this category:
Match-score level fusion: In this level of fusion, match scores generated by multiple classifiers pertaining to different modalities indicating degree of similarity (differences) between the input and enrolled templates are consolidated to reach the final decision. Integration of information at the matching score level is preferred in many applications as it offers the best tradeoff between information content and the ease in fusion.Match-score level fusion: In this level of fusion, match scores generated by multiple classifiers pertaining to different modalities indicating degree of similarity (differences) between the input and enrolled templates are consolidated to reach the final decision. Integration of information at the matching score level is preferred in many applications as it offers the best tradeoff between information content and the ease in fusion.
Rank level fusion: In rank level fusion, each biometric sub-system assigns a rank to each enrolled identity and the ranks from the subsystems are combined to obtain a new rank for each identity. Ties are broken randomly in this level to arrive at a strict ranking order and the final decision is made based on the combined ranks leading to computational complexity.
Decision level fusion: Decision level fusion is performed using the decisions output by the biometric matching components. Final Boolean result from every biometric subsystem is combined to obtain final recognition decision. In multi-modal biometric systems, final decision is made by obtaining individual decision of different processed biometric characteristics. The final results of multiple classifiers are combined via techniques such as majority voting. This level fusion is also called abstract level fusion as it uses decision from individually processed biometric modality. Fusion at this level is assumed to have loosed its rich contents before final decision is taken. Hence, it may not yield good result.
Hybrid level fusion: Hybrid category consists of fusion levels in which more than one fusion level are included. This can occur when different levels of fusion take place in different levels of system. For example, an arrangement in which two Speaker recognition algorithms are combined with three face recognition algorithms at the match and rank levels. Thus, the system having multi-algorithmic as well as multiple modalities in its design. From the investigation, integration at the feature level should have be more effective and provide better recognition results than other levels of fusion because the feature set contains richer information about the input biometric data than any other levels. However, integration at this level is difficult to achieve in practice because concatenating two features at this level may result in a feature vector with very large dimensionality leading to dimensionality problem. Very few researchers used fusion at feature level due to its complexity in mapping the compatibility of computation of different biometric character and larger dimensions in fused features. Consequently, integration of information at the matching score level is preferred as it offers the best tradeoff between information content and the ease in fusion [9,10].
Biometric information fusion methodologies
Since multiple biometric systems are designed to use more than one source or trait of biometric characteristics, fusion methodology that will effectively and efficiently consolidates these evidences cannot be over emphasized. In this section, four different information fusion techniques based on their pragmatic characteristics, robustness and reliability were comparatively presented.
Linear summation rule
Linear summation rule also known as the simple summation rule is the most common combination scheme for combining score values from multiple systems. The scores from different systems is however required to be standardized. The standardization is learned from development dataset by estimating distributions score values from each system. The scores are then translated and scaled to have zero mean and unit variance [12-14]. The simple sum rule adds the scores of each classifier to calculate the fused score. This can be expressed in the equation stated below:
Where Si is the score from the ith classifier, assuming N classifiers.
Logistic regression
Another linear combination technique is the Logistic Regression, this technique assigns weights to each classifier’s score. In this method, the weight ωi given to the i-th classifier correspond to the means difference of the distributions for client and impostor scores for the i-th classifier. The system performs better when the distributions relative to the clients and impostors are more separated and when their variance is smaller. In this case, the combination of two classifiers, S’j for the test j, can be defined as a weighted sum rule as presented in equation 2:
j=2
S’j = ∑ωιS’j
i=1 ….……………………… Equation (2)
Meanwhile, sometimes logistic regressions are difficult to interpret. Additionally, adding more variables to the model can result in overfitting, which reduces the generalizability of the model beyond the data on which the model is fit.
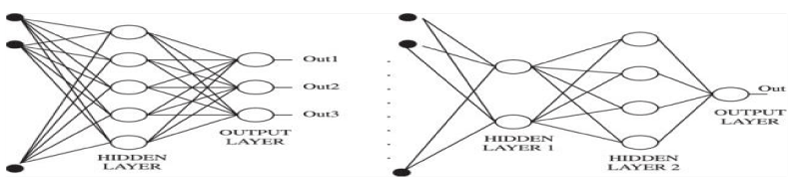
Multi layer perceptron
Multi Layer Perceptron (MLP) is a supervised learning algorithm capable to learn non-linear models. It is a class of feedforward Artificial Neural Network (ANN) that utilizes a supervised learning technique called backpropagation for training. They composed of an input layer, an output layer that makes a decision about the input, and in between those two, an arbitrary number of hidden layers that are the true computational engine of the MLP [11,15]. MLP is different from logistic regression, in that between the input and the output layer, there can be one or more non-linear layers, called hidden layers. Figure 3 shows example of MLP with scalar output.The perceptron rule is proven to converge on a solution from a finite number of iterations. In this case, MLP can be used to fuse the scores from two sources. The scores from these sources are considered as input features for the MLP classifier which are trained with client and impostor score samples on the development set. The hidden and output layers (the computational layers) are used with a double sigmoid as activation function as represented in equation 3.
MLP is a popular machine learning solution, finding applications in diverse fields such as speech recognition, image recognition, and machine translation software, but faced with strong competition. For instance, the perceptron can only learn simple problems. Meanwhile, it can place a hyperplane in pattern space and move the plane until the error is reduced. But, unfortunately this is only useful if the problem is linearly separable. This complexity has weakened this technique.
Dempster’s shafer rule of combination
Another technique which is widely studied in classical classifier fusion but less applied in biometrics is the Dempster’s rule of combination from the original conception of Dempster-Shafer Theory (DST) [16]. Dempster-shafer Rule of combination as proposed in Dempster Shafer Theory (DST) is a mathematical theory of evidence that provides a useful computational scheme for combining information from multiple sources [17]. It is a powerful tool for combining accumulative evidences and can update its priors regularly with the presence of new evidences in the database [6]. The evidence theory has been successfully applied in artificial intelligence systems, data fusion and pattern recognition [18].
The traditional interpretation of Dempster’s rule is that it fuses separate argument beliefs from independent sources into a single belief [19]. It is an associative and commutative operation that maps a pair of belief functions defined both on the same space say Ω into a new belief function on Ω’. For instance, let bel1 and bel2 be two belief functions on Ω, with m1 and m2 as their related Basic Belief Assignments (bba’s). The combination (called the joint m1,2) is calculated from the aggregation of two bba’s m1 and m2 [20]. If A and B are used here for computing new belief function for the focal element C. Then their bel1 and bel2 can then be defined through its related bba m1 and m2 as follows:
m1,2( ) C = ∑m1( )A Xm2( )B ,∀C∈Ω
A B C∩ =
1 -K ………..Equation (4)
The same result in equation (4) above can be conveniently represented with the commonality function as stated in equation (5):
∑m1( )A Xm2( )B
A B∩ =θ …………. Equation (5)
In all the four techniques presented, Dempster Shafer’s rule of combination is considered pragmatic enough particularly in high security applications. The evidence theory has been successfully applied in artificial intelligence systems, data fusion and pattern recognition systems, practically in [11,17,21] with good upshoot.
Conclusion
The quest for a viable fusion scheme to combine the evidences obtained from multiple sources and traits (Multiple Biometric) motivated this research work. The work investigated different classifier fusion schemes and design scenarios that are viable for reliable biometric recognition system. Based on the investigation on performance characteristics and application scenario, Dempster Shafer’s rule of combination and fusion at the match-score level were considered the preferred information fusion technique and design scheme respectively.
Acknowledgment
Special acknowledgement to Tertiary Education Trust Fund (TETfund) and Adekunle Ajasin University, Akungba-Akoko, Ondo State, Nigeria for sponsoring this research work.
- Ashok J, Shivashankar V, Mudiraj PVGS. An Overview of biometrics. International Journal on Computer Science and Engineering (IJCSE). 2010; 2: 2402-2408. http://bit.ly/2HP2v4v
- Jain AK, Ross A. Introduction to biometrics. 2008. Handbook of Biometrics. Springer. 2008; 1-22. http://bit.ly/386Gd9m
- Poddar A, Sahidullah M, Saha G. Speaker verification with short utterances: A review of challenges, trends and opportunities. IET Biometrics. 2018; 7: 91-101. http://bit.ly/2Tc7wtc
- Aranuwa FO. Multiple biometric systems: Design approach and application scenario. Elixir International Journal for Computer Science and Engineering. 2014; 73: 26015-26019. http://bit.ly/37SfFZf
- Thakkar D. Multi biometric fusion techniques improving identification. Bayometric. 2019. http://bit.ly/2SUgKLM
- Soliman H, Mohammed AS, Atwan A. Feature level fusion of palm veins and signature biometrics. International Journal of Video & Image processing and Network Security IJVIPNS-IJENS. 2012; 12: 28-39. http://bit.ly/2HVJ75P
- Jain AK. Microsoft® Encarta® 2008 ©, 1993-2007-Microsoft Corporation.
- Sanderson C, Paliwal KK. Information fusion and person verification using speech and face information. Research Paper IDIAP-RR. 2002: 2-33. http://bit.ly/37QF9pF
- Alsaade F, Rahmoun A, Zahrani M. On improving multimodal biometrics verification using genetic Algorithms in E-MEDISYS. 10 Conference Programmme. 2010.
- Haghighat M. Abdel Mottaleb M, Alhalabi W. Discriminant correlation analysis: Real time feature level fusion for multimodal biometric recognition. IEEE Transactions on Information Forensics and Security. 2016; 11: 1984-1996. http://bit.ly/38UMSo3
- Aranuwa FO, Olabiyisi SO, Omidiora EO. An Intelligent classifier fusion technique for improved multimodal biometric authentication using modified dempster-shafer rule of combination. Computing, Information Systems and Development Informatics Journal (CISDI). 2013; 4: 1-8.
- Jiang H, Xu dong W, Yang D, Mu ming P, and Xiao hui Z. An arithmetic rule for spatial summation of excitatory and inhibitory inputs in pyramidal neurons. PNAS. 2009; 106: 21906-21911. http://bit.ly/2Vos8Bd
- Bradley SA. counterexample to three imprecise decision theories. Theoria.2019; 85: 18-30. http://bit.ly/3a0aRCv
- Bradley S. How to choose among choice functions. Proceedings of the Ninth International Symposium on Imprecise Probability: Theories and Applications.2015;57-66. http://bit.ly/2HTTsPP
- Wei Huang, Kin Keung Lai Yoshiteru Nakamori, Shouyang Wang. Forecasting foreign exchange rates with artificial neural networks: A review. International Journal of Information Technology and Decision Making. 2004; 3: 145-165. http://bit.ly/2ThZjDM
- Smets P. Data fusion in the transferable belief model. Universite Libre deBruxelles. 2000.
- Brest B. Workshop on theory of belief functions. 2010.
- Guan X, YI X, HE Y. An improved dempster shafer algorithm for resolving the conflicting evidences. International Journal of Information Technology. 2005; 11: 200 -205. http://bit.ly/2TguuiK
- Josang A, Pope S. Dempster’s rule as seen by little colored balls. Willey Publications. 2012. http://bit.ly/38ZIzrD
- Dempster AP. Workshop on theory of belief function.
- Aranuwa FO. Multilevel decision threshold authentication mechanism for efficient multimodal biometric systems. Elixir Bio Tech. 2016: 92; 38702-38705. http://bit.ly/38TvmAC

Sign up for Article Alerts